CornCon 7 Crypto Challenge CTF Writeups
The annual CornCon conference was held Sept 10-11, 2021 and the Crypto Challenge CTF featured challenges that could all be done in a remote fashion, allowing for a great opportunity for SecDSM members to participate in the conference remotely.
There were a total of 10 challenges presented, which followed the CornCon 7 theme of “Cyber Things”, a pun/spin off of the popular Netflix series, Stranger Things.
We were able to complete the board and secured a first place finish.
Challenges
Ghost of CornCon past
Clue
Themes are important. So is remembering where you came from.
What was the slogan / subtitle for Children of CornCon IV?
Solution
Knowing that “Children of CornCon” is the title for CornCon’s kids conference, this was more of an issue of figuring
out which year was CornCon 4 and finding some references to the kids track. CornCon being well known for their movie
based themes each year, I assumed the subtitle would be in some marketing material from the year.
So, being that 2021 was CornCon 7, CornCon 4 would have been 2018, so I headed over the 2018 Kids Schedule on the official CornCon website, and came up empty handed.
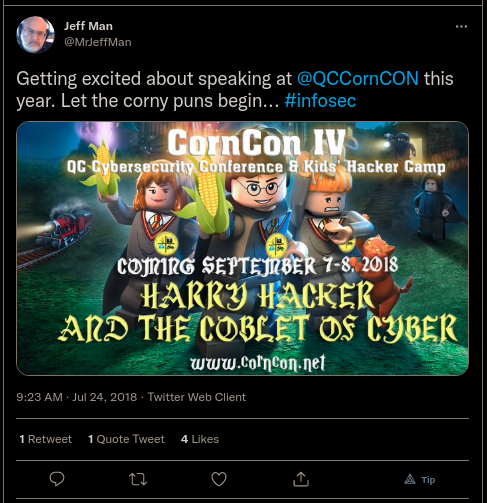
Finally, I headed over to twitter and looking for tweets from the 2018 timeframe, I came across
a tweet from @MrJeffMan which contained a subtitle
Harry Hack and the Coblet of Cyber which was the solution
As a sidenote - I actually found a challenge coin from this year for sale on ebay
Upsidedown
Clue
H4sIANgcOmEA_w3Ux66CQBTH4ScikVZcDkVEei-bCa04CNIGhKe_d3tW_5x8-T2ZVQNWWdqDAuBBB17KKSEA4ObZHmMYgm9bWPawhC93nliBPaIt9FeNVuvuKL6M5Eu8WUW6vx0KMNWVw3r6YpLAIrZc394ed8t9T8o-ZWWbwpFUTH_runeZ3HLACou3zlLovT9wI4oheZ46VrUTfOwbxPLl78asCtKiVee8XqyOidJzFhFSfVBXU6WJpAenqW2jXfYiGpG_-GIO8v3UC86KOTQJSXk0HyCe8af3uusB7VL_tikaECQ14v0RIuLwVVeJAtdCpPWY2-kn7crwYfbPiazfXKin-ooGU5a4xJnXUsmIavDSxNsRpRSESymnaAwBKmAs5EudX5Eed3nGu9NIRrzceVK3uYCA0laFi_27-Zz-Tl4rdIvTbVb1kCH0ZcOza7esIjWGLay_erZOe6sSLr4TVwyNr1OVzlbfkL4vtcCLwf6WG3sh8McY6Z-w__-5TggLvMhdR0FFbJRoR49BZtaw-95YN6G00kVAqdwrYKRx_ZIZZiBCbWqa_kVzbCg4zpv9P2TlwS-_3-VFL7W694YuoSs_bGvEkTn1C60r8aDBjsr6hgvEG5Fq7gzPh5-XWRKJ-Vl3AQZ9fbz7Jnr2JnqzVPGdWPE-eQk-Mwna5IMIvxd49KQ1QYwN_vdwRyWNv9s1DBkN-GWSXYq0OE7xg5-G5w9-RejXCiDqezKckvyO1RMSc9U1Lt1HuVpwrvTM1bvhBTm_B1SGNxQL3k9v7O_oCOL0rSQrmULGyYkGh8nyr7Dn4_W3oY1wCr_T_DvsHKWxzmdASGrgiCPe1F1oKSpQonsvpd9x3R9Gr4wynAwEV4ieQ5iItiXa_GaGxv_mnH3Rxy17Ycb6NKpIwf3Fm-VboEf_a3cVyPlukQsyBloKG8Sk7fAeszF9Up84G3jz8IKVhspkOcp3uCtEYJ04mnF0r44O9EvD4jjQaDmuRqyMouPRyr88REYtvl_WaJrDjMCwqLv9kFoh1IolGyJwWRQ5lub9iSYy0MBP-hz5IB5wu2wzpGmSeLAN12Y0O6CAIrlZgYM3D_rSg0VJpjG84dWZmXae-Cpge5dEbQdtcyREotG1p8E5sbWSdW6FKWHt94o6eo6cR0fLwmVADzoqR22zZcN2fzNtl22LcJE8ynX2HvboLGfxPkqYU8LQn-X9PSdabgqGnZs1zZvazTXEVPgvAm9UH4D3UOi2eoRRYZI_FWtdiI458gUDAnwr2XxgUG-9PJYxzSa60dwiKqgWTzWss-d5nRJIZS-xq7QBYZYG9vg6otnOsPgPLbfKcN_xQzpbWS8t58k876qw6oIuybXvnln4AM4h3seC1-z_wAHwBylgTbwvBQAA
Solution
A quick “eye” of this blob, base64 was a good guess. Initially, the use of cyberchef to base64 decode the string indicated a non-ascii result.
However, CyberChef also features a “Detect File Type”, which indicated this was gzip compressed data. But when attempting to apply the “gunzip” operation an error was produced. Turns out this was due to the way the base64 was generated. If we turn this to “urlsafe” as seen in the below image, the decoding worked well.
Once we had a successful decode of the second layer, we could again use the “Detect File Type”, it was indeed gzip
compressed data. With the clear pattern, we can just continue adding the “base64 decode (url safe)” and “gunzip” combo
until we get an answer. After the conference, I re-worked this using the Jump function to avoid dropping in 46
different “operations” into cyberchef.
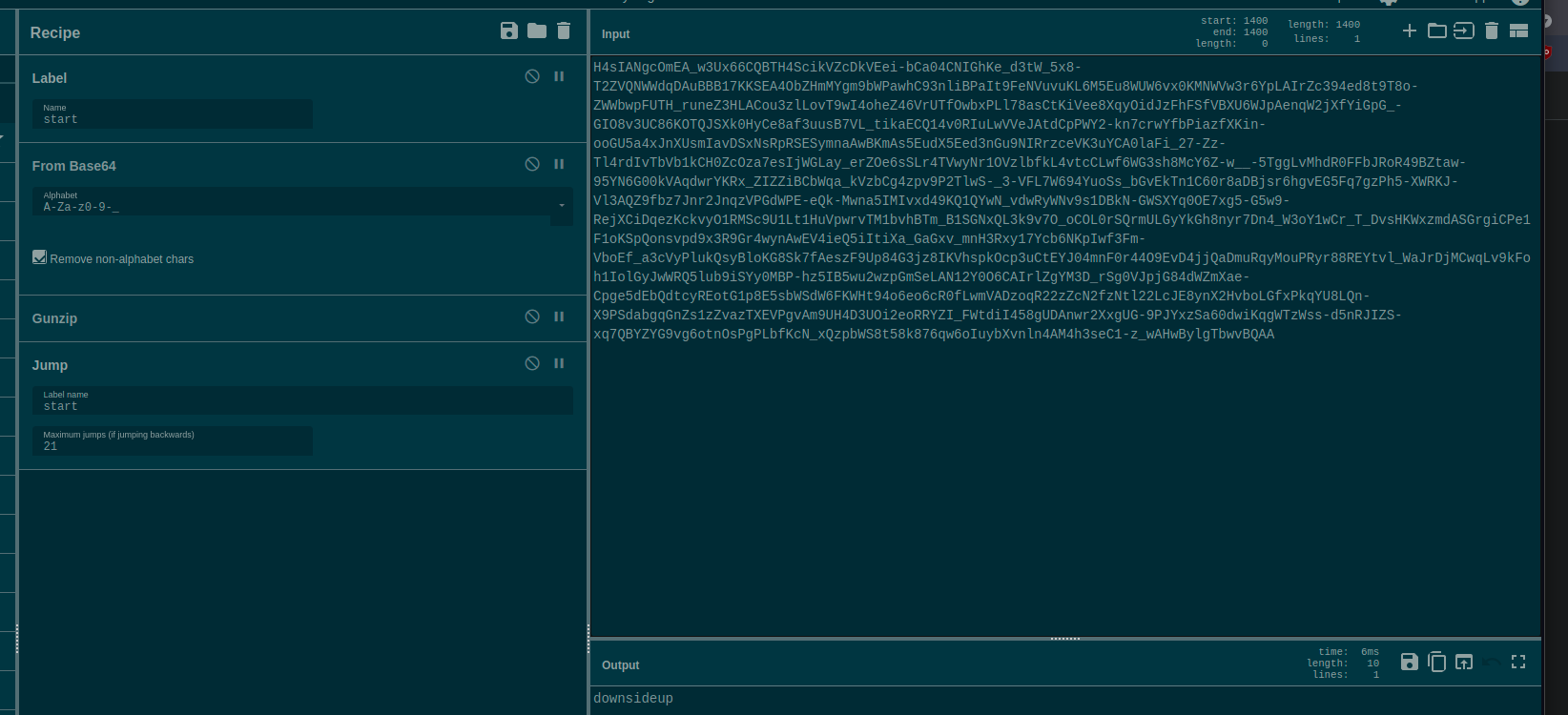
Here is the receipe in JSON format that can be loaded directly into cyberchef
[
{ "op": "Label",
"args": ["start"] },
{ "op": "From Base64",
"args": ["A-Za-z0-9-_", true] },
{ "op": "Gunzip",
"args": [] },
{ "op": "Jump",
"args": ["start", 21] }
]
Dubbel
Clue
Solve the picture
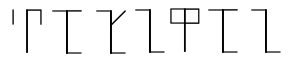
Solution
Dubbel presented itself as a substitution cipher, and a great one to get started in recognizing pattens and applying context to discover the answer.
The first observation made was that the image displays a total of seven positions and only four unique “shapes” where the shapes in position 1, 2 and 4 (from the left, going to the right) are repeated at the end of the image in positions 5, 6, and 7.
Understanding the name of the conference as context, it can be observed that Corncon is also seven positions, with
only for unique “shapes” (English letters in this case), where the letters in positions 2 and 4 are repeated in
positions 6, and 7.
Attempting Corncon as the flag, was accepted as the correct answer.
10th level Ranger
Clue
Solve the picture

Solution
10th level Ranger was a surprising difficult challenge to solve. Having a relatively low point value, after spending a about 30 minutes attempting different cipher methods (ROT13, other substitution cipher, keyed ciphers) it was decided to move along.
Finally, during the SecDSM Friday Night hangout, the group reviewed this challenge. The solution was rather simple and displayed the entire time the image was being viewed.
Looking at every other letter relieved the solution of MIND FLAYER - a clear reference to the Stranger Things theme.

A great challenge that really showed how frustrating a rather simple challenge can be when focusing on complex solutions without attempting more simple “visual” solutions.
Squiggly-wiggly
Clue
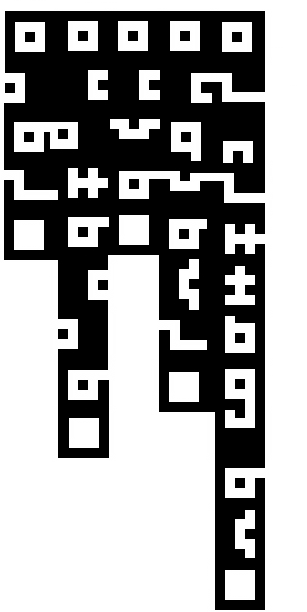
Solve the picture
Solution
Squiggly-wiggly presents itself as an image, with 5 columns of variable length, reminding me of the “Matrix” screen effect of text letters falling from the top of the screen. When looking at the first shape of each column they are constant, with no variation. Looking at the last shape of each column also reveals each ending with the same shape, distinct from the “start” shape. This reminded me a bit of “magic bytes” and “footer/trailer” bytes.
Working under the assumption these were “start” and “end” shapes, focus was placed on identifing the unique shapes in the image. Creating a grid on the image itself helped in identifying the unique shapes where the shapes were “connected”.

After creating the grid, a manual key was created and English letters were assigned to each unique shape.
A D D D C
B A F I K
C E B F C
B B E
D J L
A C M
B I
N
B
J
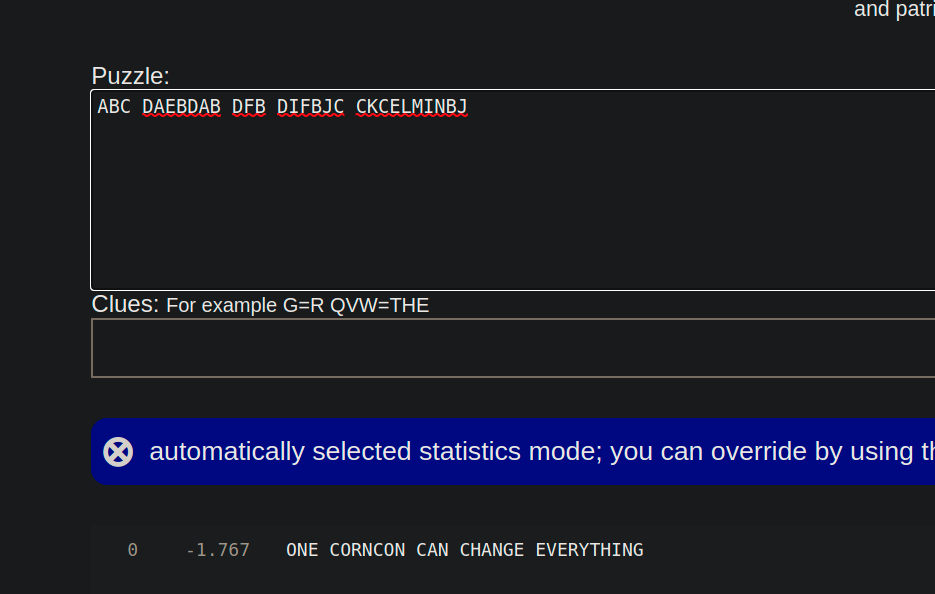
After each shape was assigned a letter, they were arranged by column into a single row, and throw into a great online tool - quipquip and solved in about a second
ABC DAEBDAB DFB DIFBJC CKCELMINBJ
Don’t Cross the Streams
Solve the picture
Provided Files

Solution
TODO
Extra Life
Clue
Solve me
For Extra Life - there were two provided files First was in image
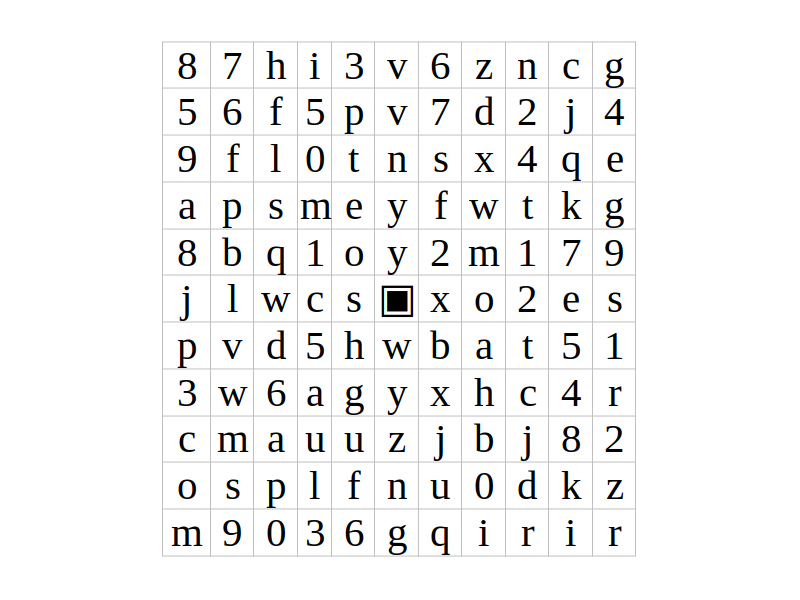
Followed by a text file containing a single line
ULULUL LDDLLDDLL LDDLLLDDL RURRUR, DLDL LUULUL LLLL LUUUULU'LUUL DDLLLLDD LLDLDD LRDD LUUULUU UURURURU RRRUURR DRRDDDD UULLL, LLDDLL DRDR LLLULLU RDRR DDRR DLLDDL RRRRRDD LLLDDDL ULLUUUU LUDDU UURRR LD RUURURRR RDDRRRR URDRRRDDUU DDRDDRD UUULR LLLLULU UUUR DRDRRDDR RDDRDDD UURUL URRURRR? UULU LUULLUUU URRRURRU ULLUUULU DDLL RRRDDDDD DLLLDDDDLL UUUULLU UUUURRRU RDR DUUDL UURRRR DDRDDRD DRDDLD LRRRDDDLLDD UULUUUL URUU UUUL RDDR RDR DRRR UULU DURR RUR DLR DRDRDDD LDDDLD DLDLLLDUUU LUDUD LLULLUL URLRRLL RUUUL LDLLDDLDL. LLULD ULU LLDDDL LDDDDLLL RRRRUU LDDDD RR RDRDRRR UUR LDLLDLDDL RDRRDRR URRURRR LULUUUU LLLLD RURRRRUU RUURUUUR URRRRRUU RUUU UDUDL, DDRRLRLDLD URRUDD URRUR LLULLU URRRRRUU DRDRDDDR LULU ULULUUU LLDDDLLD LLUUL UUUULLU RDDUUR URUURUUR. LDLD LURUU RRDDDDR ULULUUU ULLUULU LUUU RDDR LUUUUUL RUUU L UULU LDDLDLLLD RRDRRDR DLDR'LLLDDLDD RDR LLLUU DRRDDDRLLLD DRUR DRUR RUUURU ULULLLL UUUR I DRRR LULLUUUU UUULULU UURURRUU RRURUR DDDDRDR RDRR'DDULU DDL DDLDLDLLL RDDDDL DLDDRD DLLDLD RD LUU, UUUL LUULULUU UURRRRRU LURUU LUUU DDLDLLLLD DLDDLDDLLL LLL UURDUDRD DDLRDD'ULUU RDRDR DDLL RDRRDDDD URURRRUR. UURRR LD LUU RRD LUUUR L RURU RRRR DRDRRRR RDDDDRD ULLUL RDDRDRDR LU DLDRDLRDRL LLLULLU RUR ULUULUU. UUUUULL RRUURUUU LLLUUUL RRD LL RRURU, ULUUULLU RRRURUUR'UULLLU DDLLDD UURRR DRDR RDR URRRLULLU RDDRDRRD LDLDD DUL. UL DRDDRDRD RRUUR LD RRRURUUR LDLDLDLLD LLLUUU RRDDDRD LDULULDL DLDDLL DLLL LRUU DDDRRDD UDUDL ULURU DDDDR RDRR DUL DRR UUURURRU LLLD RUURR UULLLUUU RRRRUURU LDUDUUD DRRR LU DRRRDRR LRU DRDRD DLLDDD RR LRD DLDDLLDL DDRDD LLLLUU UUUULLU URRUUUUR UDRR RDDDD DRRRRDR RUU LLDD LLDLLDLD RRRDUUDRDU DRR DRLDDD RDDRRDD RRUUR UL LLLDDLDLDD UUUULLL RDDRDDD DDRDDRDR URDDURRR DDLLDLLD DRDDD DUUDULD.
Solution
Being familiar with how old cheat codes, such as the Konami Code, were shared along with a large dot in the middle of the provided grid provided a quick understanding of how to solve the challenge.
Each letter in a space seperated “word” represents a single “instruction” (quick table below), once the final instruction is hit, this represents a single letter of the word. Each word is double space seperated.
| letter | instruction |
|---|---|
| U | Up |
| L | Left |
| D | Down |
| R | Right |
As an example, the below gif walks through the first few words of this challenge.

There were two ways to solve this, manually or writing a small script/program to run through the “commands”.
During the actual CTF, the option to complete this challenge manually was selected, and being hackers, shortcuts were taken, but eventually the slow road was taken for a subset of the commands.
To facilitate completing the challenge manually, the grid was recreated in LibreOffice Calc and using the arrow keys on the keyboard to find the correct letter. A quick pattern appeared and a DuckDuckGo search allowed us to fall down a rabbit hole.
The shortcut attempted was to google the phrase that was appearing after the first few words were completed. It turned out to be a quote from Stranger Things - Season 3 episode 02
Look, all I'm saying is, what harm is there in asking? The harm in asking is that Tom will say no. We ask for forgiveness, not permission. And if this story's as good as I think it's gonna be, then Tom won't care. In fact, he'll thank us. Or the old lady is nuts and the story blows up in our face and Tom fires us.
In lining up the punctuation, everything seemed correct, but attempted submissions of this quote did not work….hmmm
The quote and the entire original clue were lined up, matching on all the punctuation to see if there were any parts that did not make sense.
ULULUL LDDLLDDLL LDDLLLDDL RURRUR, DLDL LUULUL LLLL LUUUULU'LUUL DDLLLLDD LLDLDD LRDD LUUULUU UURURURU RRRUURR DRRDDDD UULLL, LLDDLL DRDR LLLULLU RDRR DDRR DLLDDL RRRRRDD LLLDDDL ULLUUUU LUDDU UURRR LD RUURURRR RDDRRRR URDRRRDDUU DDRDDRD UUULR LLLLULU UUUR DRDRRDDR RDDRDDD UURUL URRURRR? UULU LUULLUUU URRRURRU ULLUUULU DDLL RRRDDDDD DLLLDDDDLL UUUULLU UUUURRRU RDR DUUDL UURRRR DDRDDRD DRDDLD LRRRDDDLLDD UULUUUL URUU UUUL RDDR RDR DRRR UULU DURR RUR DLR DRDRDDD LDDDLD DLDLLLDUUU LUDUD LLULLUL URLRRLL RUUUL LDLLDDLDL. LLULD ULU LLDDDL LDDDDLLL RRRRUU LDDDD RR RDRDRRR UUR LDLLDLDDL RDRRDRR URRURRR LULUUUU LLLLD RURRRRUU RUURUUUR URRRRRUU RUUU UDUDL, DDRRLRLDLD URRUDD URRUR LLULLU URRRRRUU DRDRDDDR LULU ULULUUU LLDDDLLD LLUUL UUUULLU RDDUUR URUURUUR. LDLD LURUU RRDDDDR ULULUUU ULLUULU LUUU RDDR LUUUUUL RUUU L UULU LDDLDLLLD RRDRRDR DLDR'LLLDDLDD RDR LLLUU DRRDDDRLLLD DRUR DRUR RUUURU ULULLLL UUUR I DRRR LULLUUUU UUULULU UURURRUU RRURUR DDDDRDR RDRR'DDULU DDL DDLDLDLLL RDDDDL DLDDRD DLLDLD RD LUU, UUUL LUULULUU UURRRRRU LURUU LUUU DDLDLLLLD DLDDLDDLLL LLL UURDUDRD DDLRDD'ULUU RDRDR DDLL RDRRDDDD URURRRUR. UURRR LD LUU RRD LUUUR L RURU RRRR DRDRRRR RDDDDRD ULLUL RDDRDRDR LU DLDRDLRDRL LLLULLU RUR ULUULUU. UUUUULL RRUURUUU LLLUUUL RRD LL RRURU, ULUUULLU RRRURUUR'UULLLU DDLLDD UURRR DRDR RDR URRRLULLU RDDRDRRD LDLDD DUL. UL DRDDRDRD RRUUR LD RRRURUUR LDLDLDLLD LLLUUU RRDDDRD LDULULDL DLDDLL DLLL LRUU DDDRRDD UDUDL ULURU DDDDR RDRR DUL DRR UUURURRU LLLD RUURR UULLLUUU RRRRUURU LDUDUUD DRRR LU DRRRDRR LRU DRDRD DLLDDD RR LRD DLDDLLDL DDRDD LLLLUU UUUULLU URRUUUUR UDRR RDDDD DRRRRDR RUU LLDD LLDLLDLD RRRDUUDRDU DRR DRLDDD RDDRRDD RRUUR UL LLLDDLDLDD UUUULLL RDDRDDD DDRDDRDR URDDURRR DDLLDLLD DRDDD DUUDULD.
L o o k , a l l I 'm s a y i n g i s , w h a t h a r m i s t h e r e i n a s k i n g ? T h e h a r m i n a s k i n g i s t h a t T o m w i l l s a y n o . W e a s k f o r f o r g i v e n e s s , n o t p e r m i s s i o n . A n d i f t h i s s t o r y 's a s g o o d a s I t h i n k i t 's g o n n a b e , t h e n T o m w o n 't c a r e . I n fact, he'll thank us. Or the old lady is nuts and the story blows up in our face and Tom fires us.
The error became apparent in this process around this point.
RDRDR DDLL RDRRDDDD URURRRUR. UURRR LD LUU RRD LUUUR L RURU R
c a r e . I n fact, he'll thank us. O
As determined by the double space, after the sentence ending with “care.”, a three-letter word is expected, however the quote only has a two-letter word. As such, back to manual decoding of the commands.
UURRR LD LUU RRD LUUUR L RURU RRRR DRDRRRR RDDDDRD ULLUL RDDRDRDR LU DLDRDLRDRL LLLULLU RUR ULUULUU.
the answer is konami.
Submitting the flag of konami indicated a correct answer.
Lab Homework
Clue
One of the sensors on the Hawkins National Laboratory’s public facing dashboard is displaying some weird unreadable messages. Can you take a look?
Dashboard: 54.80.132.176
Solution
In visiting the IP Address via the web browser we’re presented with a dynamically updating dashboard.
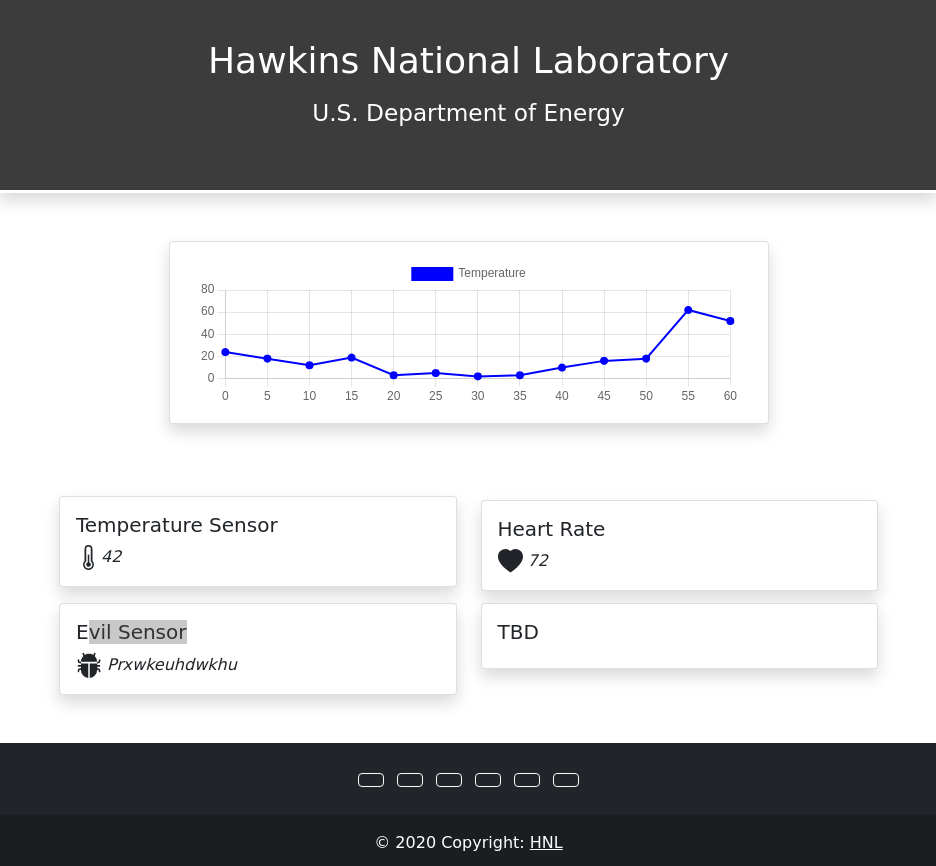
Noticed the “Evil Sensor” with some gibberish displayed, but before tackling that, a review of the HTML/Javascript was conducted in an attempt gather context for any other clues.
Upon looking at the HTML, it was clear that the page was using a javascript library called Eclipse Paho JavaScript client to connect to and receive messages from a MQTT server. The javascript would receive the messages, inspect the messages for which sensor it was for and then update the sensor’s text on the page.
In order for this to function, the receiver actually “subscribes” to which “topics”, and then declare which function to run when new messages were received.
// once we conenct, subscribe to the "sensor"
function onConnect(){
console.log("Connected");
mqtt.subscribe("sensor/#");
}
Upon seeing this, the first attempt to find the solution was to subscribe to all topics. Quickly downloading the HTML and correctly “relative” references to the absolute paths which included the remote ip address of the server, the HTML page could be rendered and modified locally. This allows for a quick development environment where the code could be manipulated without running a webserver or any other software beyond a web browser.
After quick DuckDuckGo, and a primer on MQTT topic levels subscribing to all the topics was a quick change.
// once we conenct, subscribe to the "sensor"
function onConnect(){
console.log("Connected");
mqtt.subscribe("#");
}
However, nothing new was presented. After learning a bit about MQTT and gaining all the context of how the dashboard was working, attention was focused back on the text being displayed on the “Evil Sensor”
Prxwkeuhdwkhu
One very useful item for determining if a key based encryption is used, or a more simple substitution/rotation cihper is to examine the entropy of the string. Given this string is 13 characters long, and we suspect the flag would be in the English letters. Thankfully, CyberChef has a recipe for this, and we can quickly get this.
Entropy pretty much measures out “random” something is on a scale of 0 (no randomness) to 8 (perfectly random). Encryption creates randomness, substitution/simple rotations don’t change the “randomness” of a string.
CyberChef shows the Shannon Entropy for this input at 3.0, petty darn low. This leads the direction of not being a keyed encryption method. A good first guess is something like Caesar Cipher and it’s friend ROT13.
In this case, CyberChef can also be used to “roll though” the different shift options and some clear text is found at ROT23
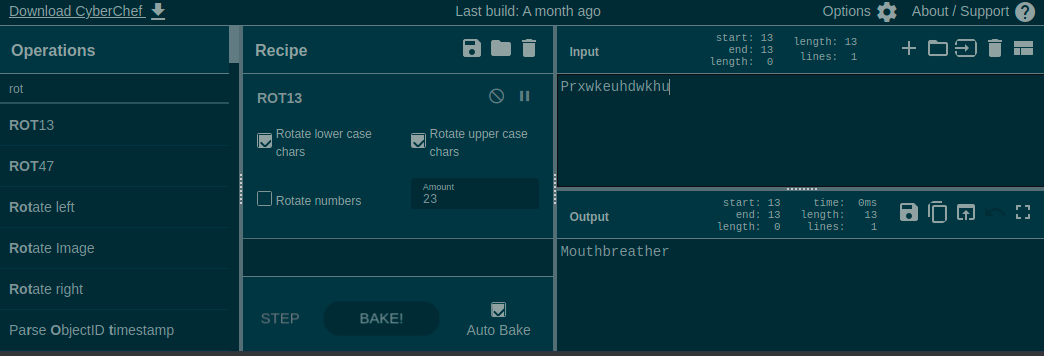
Mouthbreather
Coming back to Entropy for just a bit. It’s an interesting concept with a boatload of uses within information security. I went back with our answer and ran it through a few different methods just to see what the Shannon Entropy would be for them.
| Method | Entropy |
|---|---|
| Plain Text | 3.085 |
| ROT23 | 3.085 |
| Single byte XOR | 3.085 |
| Vigenère | 3.335 |
| Multiple bye XOR | 3.700 |
| AES-ECB | 4.0 |
| AES-GCM | 5.11 |
| RSA 1024bit Key | 6.560 |
| RSA 2048bit Key | 7.072 |
| RSA 4096bit Key | 7.59 |
Overall, a very fun challenge with tons of learning opportunity. Looking forward to seeing this challenge being used next CornCon and working multiple challenges into the Dashboard concept!
Typo Squatting
Clue
What is in my traffic?
Provided Files
Solution
TODO
Don’t Blink
Clue
Solve the animated pic
Provided Files
Solution
TODO
What’s your Vector, Victor?
Clue
Our sensor network detected an anomalous power surge at 1500. We were able to calculate the source to a location just behind Hawkins Library.
Please use the data to help us calculate where the power spike occurred at 0330.
Provided Files
Hawkins_Map.jpg hawkins_stats.csv
Solution
TODO
Junior Panda Swim Team
Clue
Solve the text
Provided Files
Solution
TODO
Influencer
Challenge
I was driving through town making a video for my YouTube channel and I heard something wierd come across the radio...
Can you help me figure out what it was? Until then, I'm just going to post the video without any sound.
Provided Files
Solution
TODO
Town Square
Clue
We recovered this file from the remains of the lab, but it appears incomplete.
Maybe you can fix it and help us solve the mystery.
Provided Files
Solution
TODO